Summary of Steps:
- Follow the doc for RDP
- Install Duo for Windows
- Set up user
- Set up MFA device (your phone)
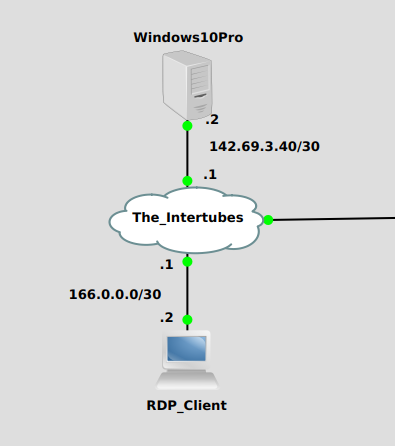
It’s actually fairly quick and painless to get set up with Duo MFA for Windows, with the exception that you have to manually add a user and enroll your phone. With SSH on Linux there was some editing of text files, compiling code and command-line stuff, but with Windows it’s lots of clicking of those old familiar friends, “Next”, “Ok”, and “Finish”. Here is my topology:
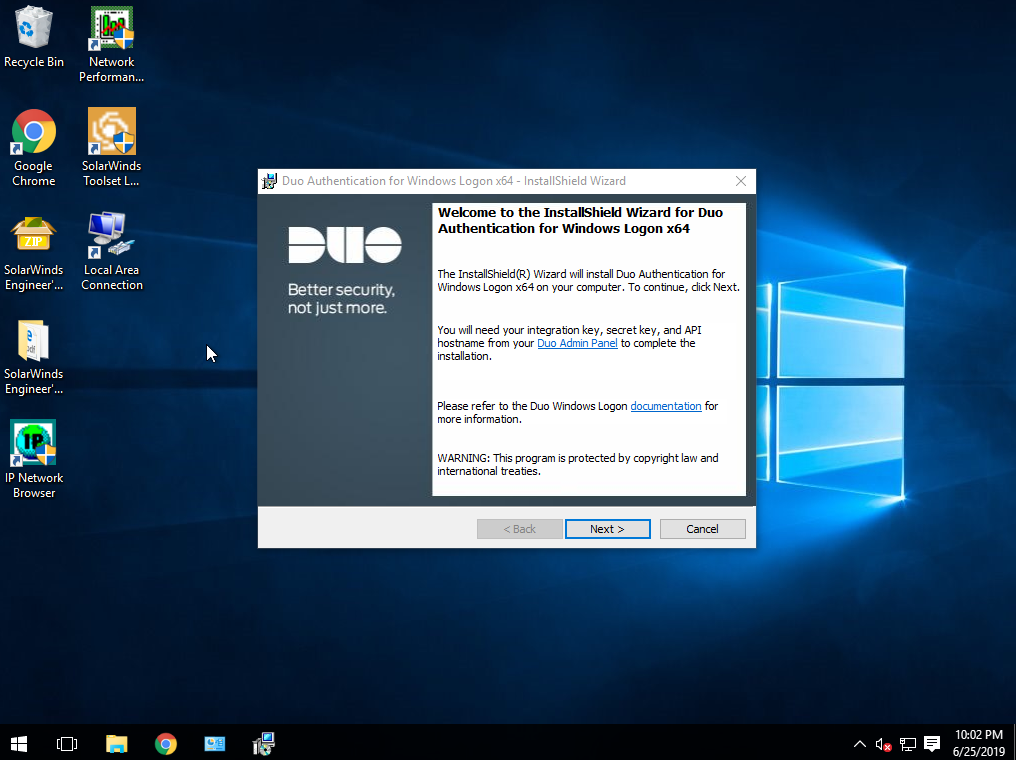
First, I log into my account dashboard at https://duo.com (for which I’m MFA prompted on my phone, of course) and go to “Applications”. I click “Protect an Application” and click “Microsoft RDP”. Reading the docs at https://duo.com/docs/rdp I download the Duo Windows installer and away I go:
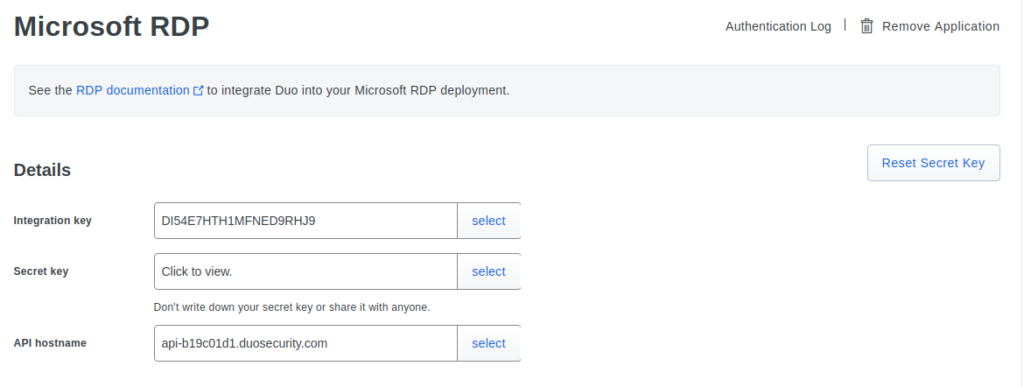
You can find the API hostname, integration key, and secret key by clicking “Protect this Application” for MS-RDP:
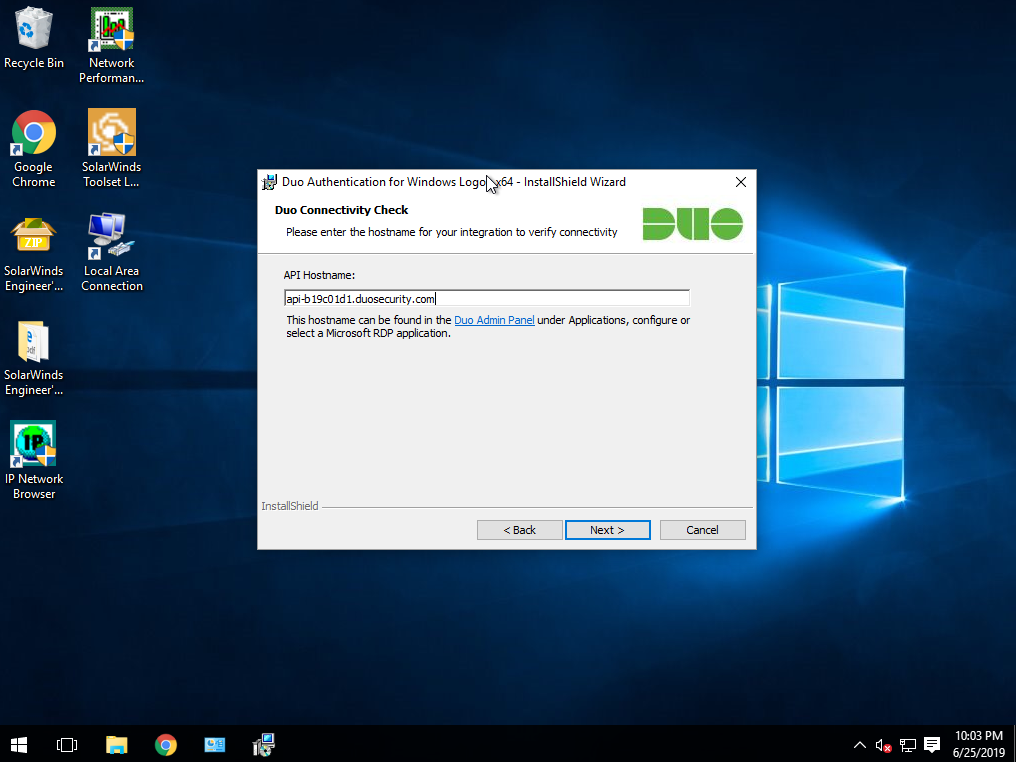
Ready to install!
And…. it’s done.
Then we need to manually add a user, as I mentioned. From the Duo dashboard, just click “Add user”. For some reason when I created this VM some time ago I name the user “solarwinds”, I think I was doing some network testing. I regret nothing.
Add my phone:
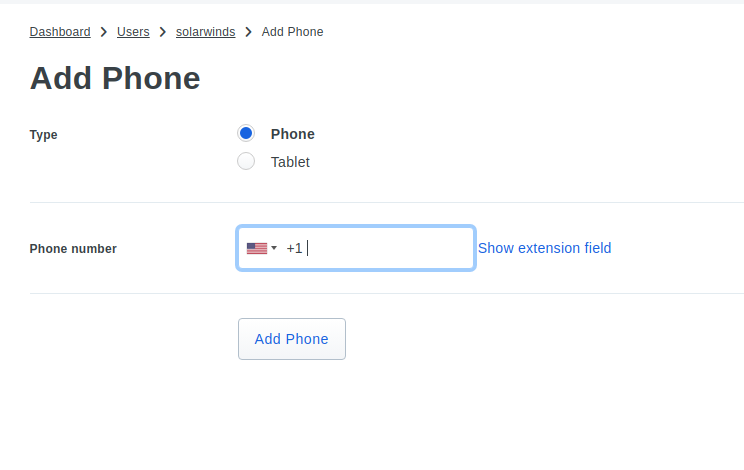
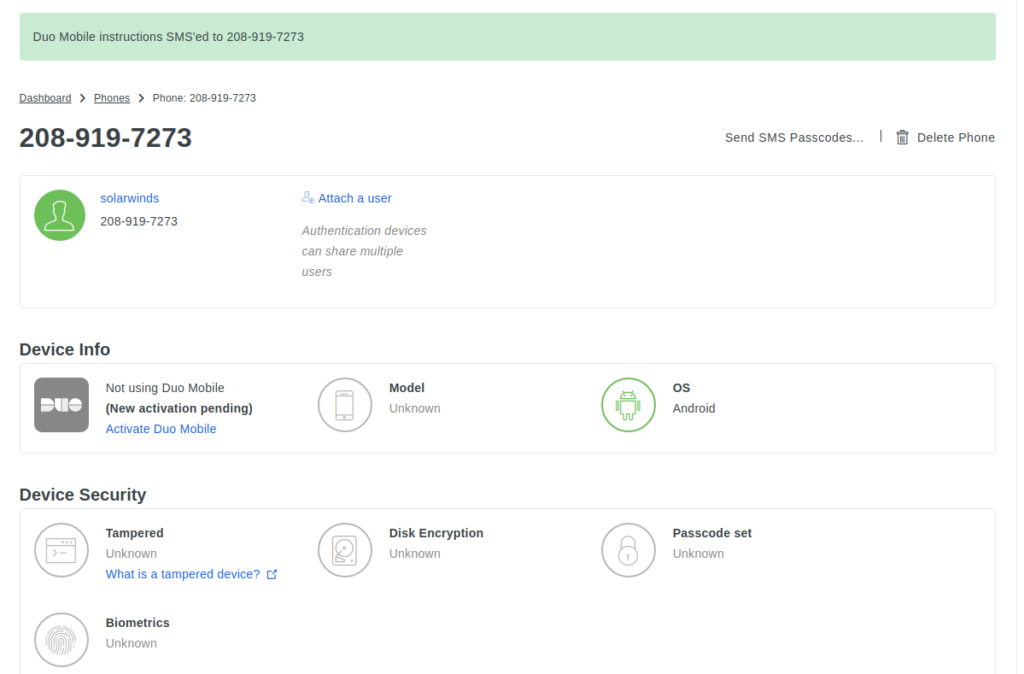
Send the activation link to you phone, and you can activate Duo Push Mobile app if you have it.
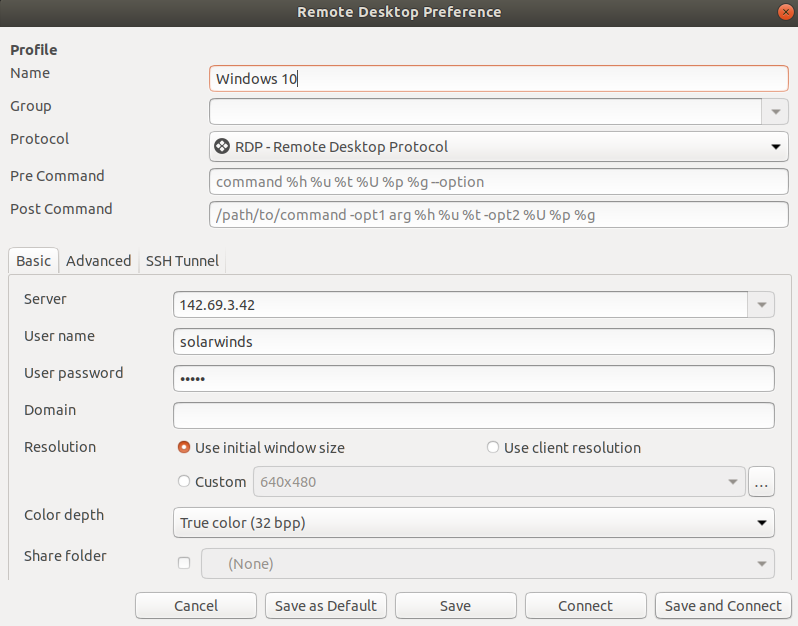
Then log in! I use Remmina on Linux, but of course any RDP client will work.
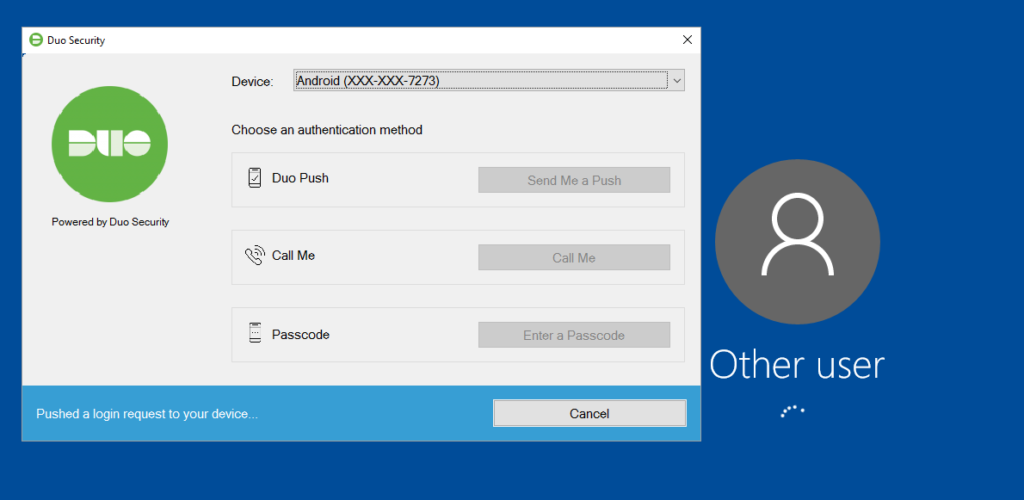
I’m prompted by Duo and a code is sent to my phone:
And I’m logged in!
There is much rejoicing.
